Active Directory has changed a lot since it’s birth in 1999. The first time I used Active Directory was around 2004 on a Windows 2003 server. We had an Exchange 2003 server, and I remember using active directory to create e-mail accounts. Back then, AD was basically just the “Active Directory Users, and Computers” snap-in, and a few other components. Up to this day, when I think about AD the thought of account authentication, users and computer management, etc. are interchangeably, but as we will see, AD is not just about authenticating users or managing resources anymore, it has become a bigger beast featuring many roles and services.
Table of Contents
In this tutorial I’ll go over the basics of AD then I’ll go over each AD role in Windows Server 2016, and maybe installing and playing with the roles later on. As always, the best way to learn something is by doing it, so if you have time, install AD in a Windows 2016 server and play with it. Here are some tutorials to get you started with that:
What is Active Directory?
If you are new to Active Directory I guess the first question you have is, what is Active Directory? at the most basic level, Active Directory is a hierarchical database that keeps track of user accounts, computers, certificates, security policies, and other resources in a computer network. Before AD was created by Microsoft, computers were standalone devices and hard to manage. For example, imagine we are in the year 1998 right now, and you are the systems administrator for a company of 300 people, and you need to install a new printer for all employees in the office, how you go doing that? because all computers are standalone you have to install the driver for the new printer in all 300 computers manually, one by one. That would be a lot of work to accomplish a simple thing. A lot of things that we systems administrators take for granted today like file and print sharing, network group policies, etc. weren’t possible before active directory. so in essence, AD is that, a hierarchical database that makes it easier to manage user accounts, computers, and other network resources from single point location.
How does Active Directory work?
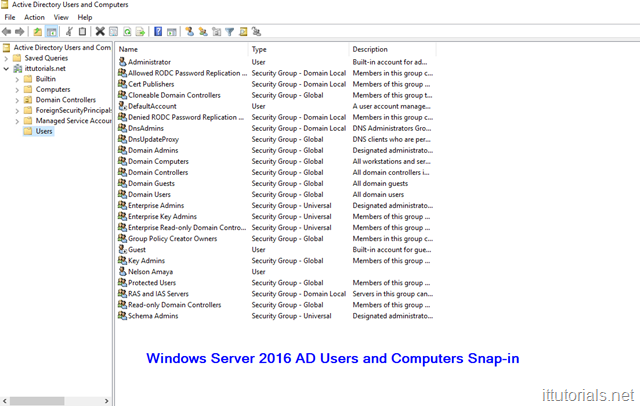
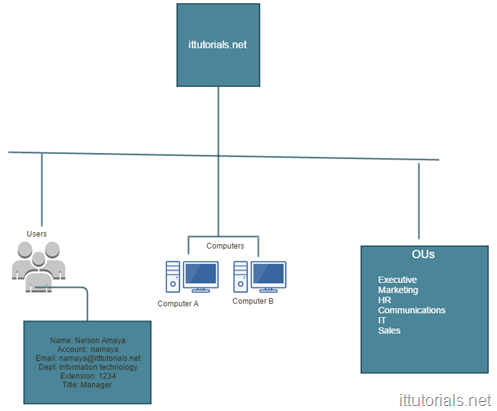
The way I have always picture AD is that of a phone book. A phone book basically matches names to phone numbers, Active Directory matches user accounts to network objects and resources. Unlike phone books though, AD can keep information about organizations, sites, systems, users, shares, and many other things, so AD is more flexible than a phone book but the concept is similar. One significant difference of AD is that it saves objects in a hierarchical order, and all objects are unique. that’s why a domain name is required when installing AD, all objects in a domain forest are “sub domain” or children of the top domain. For example, If I create a user called “Nelson” in my AD it will be saved as “[email protected]”, if you try to create the same account again, you will get an error saying there is an object already in the network with the same name.
Active Directory Components
When discussing or learning Active Directory there are some terms you need to be familiar with:
- Domain Controller a domain controller is the server where AD is installed. Sometimes the term Active Directory and Domain Controller is used interchangeably.
- Forest A forest is the highest level of the logical structure hierarchy. An Active Directory forest represents a single self-contained directory. A forest is a security boundary, which means that administrators in a forest have complete control over all access to information that is stored inside the forest and to the domain controllers that are used to implement the forest
- Tree Trees are a cohesive group of domains, known as subdomains or child domains, that grow from a root domain. All the domains within a tree share a contiguous namespace
- Schema The Active Directory schema contains definitions for all the objects that are used to store information in the directory. There is one schema per forest
- operations masters or FSMO roles There many FSMO roles in AD but the most popular one is the Primary Domain Controller (PDC) and Backup Domain Controller (BCD) role. The Primary Domain Controller maintains the master copy of the directory database and validates users. A Backup Domain Controller contains a copy of the directory database and can validate users. If the PDC fails then a BDC can be promoted to a PDC. Possible data loss is can happen if changes that have not yet been replicated from the PDC to the BDC. A PDC can be demoted to a BDC if one of the BDC’s is promoted to the PDC
- Global Catalog (GC ) Server The global catalog is a distributed data repository that contains a searchable, partial representation of every object in every domain in a multidomain Active Directory Domain Services (AD DS) forest. The global catalog is stored on domain controllers that have been designated as global catalog servers and is distributed through multimaster replication. Searches that are directed to the global catalog are faster because they do not involve referrals to different domain controllers.
- AD relies heavily in the DNS system too, that’s why you can’t install active directory without choosing a domain name first. Unlike a website, the domain when installing active directory does not need to be unique, but if you have a public domain name it is recommended to use the same name when installing AD. for example if your public website is ittutorials.net then your AD domain name could be “ad.ittutorials.net” or something like that. This domain name will become your “domain forest” once the AD component is installed successfully in the server. AD requires a DNS server, but if you don’t have one already installed when installing AD you can choose to make that server a DNS server as well. If you are setting up Active Directory for a production environment is always recommended to setup two domain controllers at least.
Active Directory Roles in Windows Server 2016
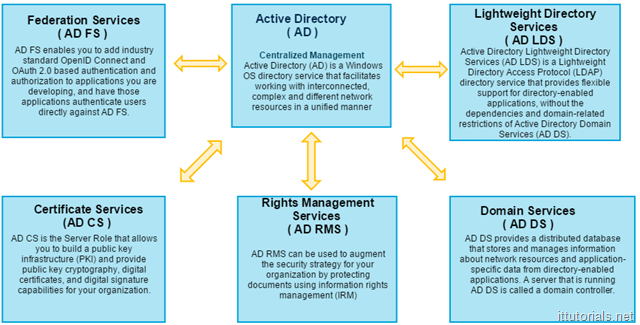
So far we have focus almost just in the domain services role which is the role AD is mostly identified by. But in Windows Server 2016 as in previous Windows server versions, there are five individual roles that make up active directory:
- Federation Services ( AD FS ) This role is necessary if you need to authenticate applications or services outside your network. for example, a few months ago we signed up for Facebook Workplace, and we wanted to authenticate users against our AD. Using this role I was able to connect the application using the OSS and the SAML protocol.
- Lightweight Directory Services ( AD LDS ) Most of us are familiar with this role because we use LDAP a lot. When Kerberos authentication is not possible we rely in LDAP to authenticate application or services against AD
- Certificate Services (AD CS ) This role is responsible for managing certificates and other cryptographic components in your network. When you install a certificate in your network you use this role.
- Rights Management Services ( AD RMS ) this role provides persistent data protection by enforcing data access policies. For documents to be protected with AD RMS, the application the document is associated with must be RMS-aware
- Domain Services ( AD DS ) This is the main role in active directory. it stores and manages information about the network resources.
How do I enable Active Directory roles in Windows Server 2016
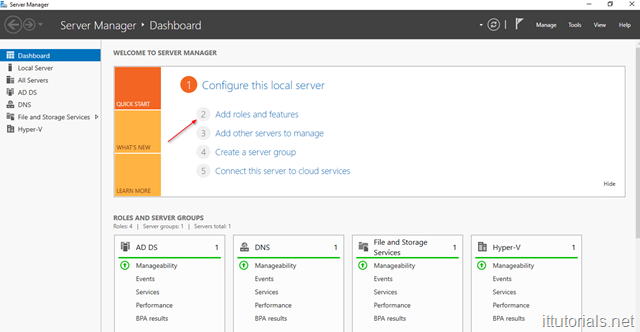
When you promote Windows Server 2016 as a domain controller the DS service gets installed by default. If you need to install other roles do this:
Login to your server, and open Server Manager then click on Add roles and features:
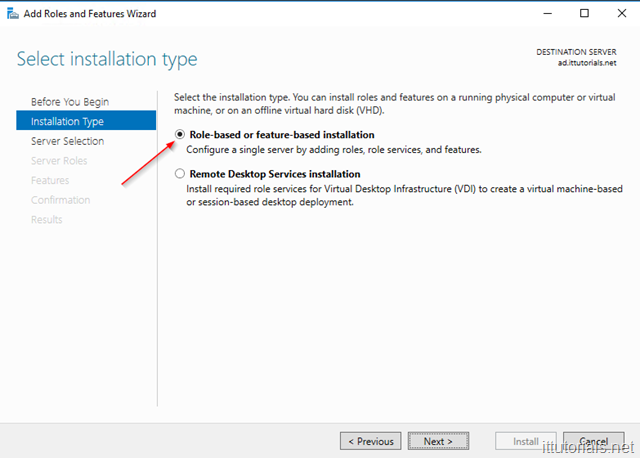
The add roles and features wizard will come up. click on Next and then on Installation type choose Role-based or feature-based installation:
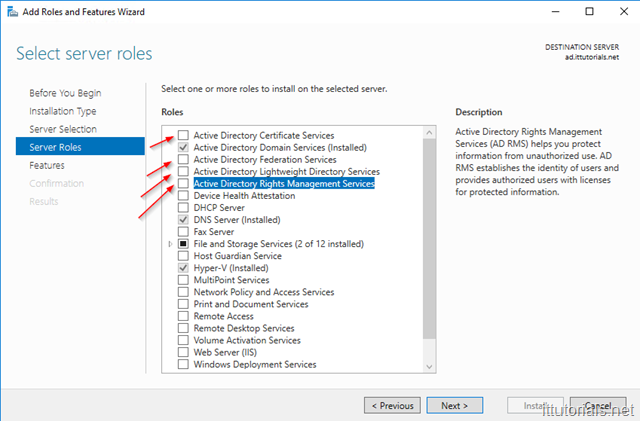
Click on Next again then select the server where you want to install the role. click Next until you get to the page where you choose the role you want to install:
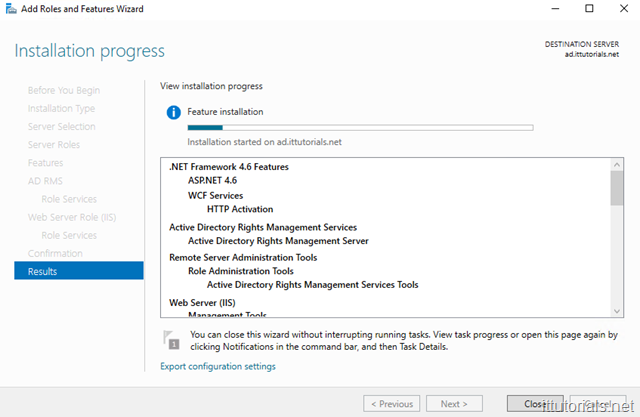
Most likely when you select a role you will get a pop-up listing all the other features that will be installed along with that role. Follow the prompts ( mostly just defaults ) until you get the screen to initiate the install:
Summary
AD is a very complex system and it takes awhile to wrap your head around it. Understanding it takes time and a lot of hands on experience. A lot of the things we do as systems administrators involves AD anyhow, it could be either group policy, permission access management, LDAP authentication, etc. I hope you find this tutorial useful, any question or comment you might have, please use the comments section below.