Email spoofing is a big security issue in IT. Often email users get fake emails pretending to be from colleagues or from their boss, and many of them fall for it sometimes leaking sensitive information to spammers.
Table of Contents
What is email spoofing?
Email spoofing is the process of forging an email address to make it look like is sent from a known email address. Basically in a spoofed email the from: field is modified to make it look like the email is coming from a person the recipient know.The result is that the email recipient sees the email as having come from the address in the From: field; but if they reply to the email it will go to Reply-to email address which is an email address the spammer might have setup to receive those replies.
Why is email spoofing possible?
The reason why email spoofing is possible and relatively easy for spammers to do is because of a vulnerability in the protocol used to transport emails through the Internet. SMTP (Simple Mail Transport Protocol) does not use any authentication mechanism for header fields like from, Reply-to, Return-Path spammers forge these headers using certain commands to make it appear that is coming from a different source than its original one.
Why spammers spoof emails?
Spammers spoof emails for many different reasons but the most common reason is to obtain valuable and sensitive information like SSNs, credit cards, bank accounts, etc.
What is the easiest way to identify a spoofed email?
The easiest way to identify a spoofed email is by examining the characteristics within the email very closely. A spoofed email will rarely address the recipient directly, and will use terms like “Hi, Hello, Good morning or formal terms like Sir or Madam, or no addressing at all. Unless the person is being targeted directly, spammers send those emails in a batch, so no one is addressed individually. Also you can identify a spoofed email by looking at the “Internet header” there you should be able to see the original source o of the email. if after checking all that you are still unconvinced that the email is fake, then call the sender on the phone and ask if she/he really sent the email. Don’t ever reply to the email if you are unsure.
As an IT person how can I block spoofed emails?
Spoofed emails are hard and almost impossible to block with spam filters alone, so don’t go crazy tweaking your spam filters trying to block spoofed emails. If you really want to block spoofed emails, you need to implement these domain based email authentication mechanisms:
- SPF ( Sender Policy Framework ) SPF is a simple email-validation system designed to detect email spoofing by providing a mechanism to allow receiving mail exchangers to check that incoming mail from a domain comes from an authorized host
- DKIM (Domain Keys Identify Mail ) as SPF DKIM is intended to prevent forged sender addresses in emails. DKIM allows the receiver to check that an email claimed to come from a specific domain was indeed authorized by the owner of that domain which is done using cryptographic authentication.
- DMARC (Domain-based Message Authentication, Reporting and Conformance) DMARC is an email validation system designed to detect and prevent email spoofing. It provides a mechanism which allows a receiving organization to check that incoming mail from a domain is authorized by that domain’s administrators and that the email (including attachments) has not been modified during transport. It is thus intended to combat certain techniques often used in spoofed emails, such as emails with forged sender addresses that appear to originate from legitimate organizations.
One important detail to keep in mind is that DMARC is built on top of the first two mechanisms, SPF and DKIM, so those two need to be implemented before implementing the DMARC record.
How do I implement those records?
All these records are implemented at the domain level using a “TXT” string record so it’s not very difficult to implement them once you gather all the information you need to do so. Things you need to know before implementing these records are:
- IP addresses of your mail servers and all authorized email senders
- Are there third party hosts that need to be white listed that you are not aware of? external newsletters and other cloud hosted applications?
Setting up SPF
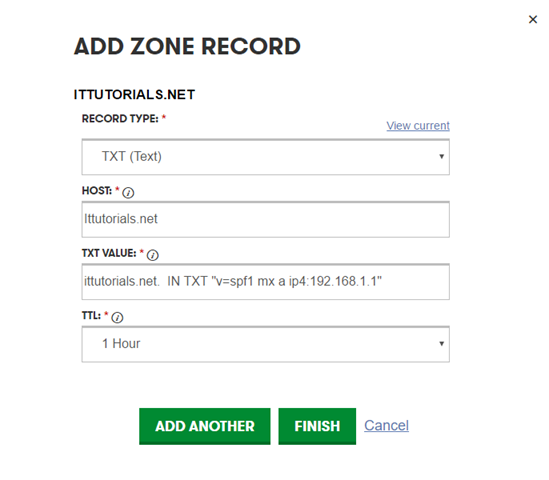
Once you gather the necessary information the first record you should implement is SPF. go to this URL http://www.spfwizard.net/ to generate the SPF record for your domain. after you enter the required information, the generated string should look like this:
ittutorials.net. IN TXT "v=spf1 mx a ip4:192.168.1.1"
Now login to your DNS manager and setup a TXT record using that information:
After you add the record, go to a website like this http://mxtoolbox.com/spf.aspx to check if the record is valid.
Setting up DKIM
Setting up a DKIM record is a little more complicated than a SPF record especially if you are hosting your own mail server like Exchange on premise. To implement a DKIM record using Exchange you need to use a third-party tool like this https://www.emailarchitect.net/domainkeys/ to generate the cryptographic keys. I haven’t done that in our mail server so I don’t know how the process is. If you are using Exchange hosted on premise but using Google Apps for spam filtering, then the process is a little easier because Google Apps can generate the DKIM record for you. to do that Login to your Google Apps management panel, and go to Apps > Google Apps > Gmail > Authenticate email select the domain from the drop down menu, and click on generate a new record. your DKIM record should look like this:
Setting up DMARC
OK so now that we have implemented the SPF and DKIM records is time to put the last nail in the spoofed emails coffin. I will advise you to go very slowly implementing the DMARC record though, once you implement a DMARC record fully, there will be no unauthenticated mail coming through, email either authenticate or will bounce back to the sender. The first “phase” should be to setup DMARC reporting only using this string “v=DMARC1; p=quarantine; rua=mailto:postmaster@your_domain.com” using that string everybody will still get all mail authorized and unauthorized, but you will get a report of all the unauthorized emails coming through so you will know the impact your company will have when the “reject’ DMARC policy is implemented. after you gather enough information and are confidant that nothing will be affected, then you can implement the “reject” policy using this string “v=DMARC1; p=reject; rua=mailto:postmaster@your_domain.com” you can find more information on how to implement your DMARC record gradually on this link
Conclusion
Blocking spoofed emails is not easy because of the SMTP protocol vulnerabilities, but by implementing the authentication mechanisms I wrote in this tutorial you can almost eliminate spoofed emails completely. I hope this tutorial gave you some insights on how to combat spoofed emails. If you have any question, suggestion or comment, please let me know in the comments. Thanks.
Was this article helpful?
Your feedback helps us improve our content.
12 people found this helpful!