Email spoofing explained and prevention
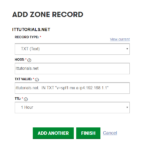
Email spoofing is a big security issue in IT. Often email users get fake emails pretending to be from colleagues or from their boss, and many of them fall for it sometimes leaking sensitive information to spammers. What is email spoofing? Email spoofing is the process of forging an email address to make it look like is sent from a…
how to create a fake change password login page

One of the best ways to keep your email users on their toes when it comes to e-mail security is to hack them before a real hacker does it first. We just went through this drill at the place I work for as a training. We sent out an email using a publicly available email address ( Gmail ) using…
