If you are a systems administrator in charge of keeping a mail server running then spoofing emails is probably one of your biggest headaches. Spoofing techniques used by spammers are becoming more sophisticated every day, many of them even employing artificial intelligence to exploit your mail system vulnerabilities.
I’ve been researching ways to combat and prevent spoofing emails for years because it always has been a big issue at the place where I work.
There are ways to minimize or even eliminate spoofing emails completely, but managing a mail system is complicated as I’m sure you are aware of, and our focus, in my opinion, should be in striking a happy medium.
So our focus shouldn’t be to eliminate spoofing emails completely but to mitigate and stay ahead of the game so the objective of spammers through spoofing emails is never achieved.
You might be wondering, why can’t we just focus in eliminating spoofing emails? and the answer is that you cannot eliminate spoofing emails without disrupting the normal legitimate mail flow. That’s why I said above, striking a happy medium is your best bet, otherwise, you might end up with a bigger self-created problem of legitimate emails being caught up in or rejected by the spam filters, mail server rejections, undeliverable messages, etc.
Remember, people don’t care much about your benevolent intentions of preventing a catastrophe caused by a spoofing email. they just care about their mail, so they will complain about spoofing e-mails, and they will complain even more when legitimate emails are not being delivered to their mailboxes in time or not at all, so you are always in a lose/lose situation if you are trying to go rogue in eliminating spoofing emails on your own.
But it shouldn’t be that way, you can make it a win/win situation if you play your cards correctly.
And your first card should be:
Education
Educating your mail users should be the first step combating spoofing emails. There are many ways you can approach educating your users, but simple email reminders reminding people that not all emails are created equal is a good start. Outline the characteristics of a spoofing email and train your users how to distinguish them from the regular mail flow. Most spoofing emails are very genetic and with a trained eye is easy to spot them. Some of them are not as easy but train your users that when in doubt to always consult with you before taking any action.
Most spammers sending spoofing emails are after either money or private personal information like social security numbers. So make sure the finance and HR departments have processes in place for disbursing money and handling personal private information.
That could be your first “cover my ass” plan.
The reality is that when the shit hits the fan, the first person they will go to for answers will be you, but if whoever fell for the spoofed email didn’t follow the proper procedure, then you will have something to fight back.
Of course, the objective should be to never get to that point, but if you have been working in this field long enough then you know that
Shit happens.
So after you get the education thingy going, what should be the next step?
Get to work goddamnit!
No, I’m just kidding. Before we proceed though, I can’t emphasize enough that educating your users is the most crucial step, and its a lot of work because most people don’t like hearing the IT guy talk about like its gonna be the next world war if they click on a suspicious email, so it’s hard to grab their attention, so yeah, its a lot of work to get your message across, but after awhile they’ll get it.
So let’s get into some technical stuff now.
The four technical components that will help you fight spoofing emails are:
- Spam Filtering Software
- SPF
- DKIM
- DMARC
We will go through each of this component individually.
The spam filtering software is a given. with the amount of spam hitting your mail server I wonder how it would be if you didn’t have a spam filter, right?
Most spam filters are cloud-based now with many of them using artificial intelligence and machine learning to adjust to new spamming trends quickly, so if you are not using a cloud-based spam filtering software yet, start looking into it.
SPF or Sender Policy Framework is a DNS entry that you create in your domain that prevents other domains from using your domain to send emails as you. In other words, an SPF record is designed to prevent spoofing emails.
SPF was invented in early 2000 and is considered indispensable for fighting spam nowadays. The record you add to your DNS should look like this:
“v=spf1 a:ittutorials.net -all”
In this example, only the “ittutorials.net” domain is authorized to send emails. The record will check for “ittutorials.net” IP address, including the “reverse DNS” IP to make sure the email is authentic.
If it finds anomalies in any of those things, it will reject the emails, so make sure your Reverse DNS is set up properly.
If you are not sure what Reverse DNS is, call your Internet provider and ask them, they will set it for you if don’t have it.
There is a tone of information online about SPF and how to set it up properly so hit Google if you need more info about it.
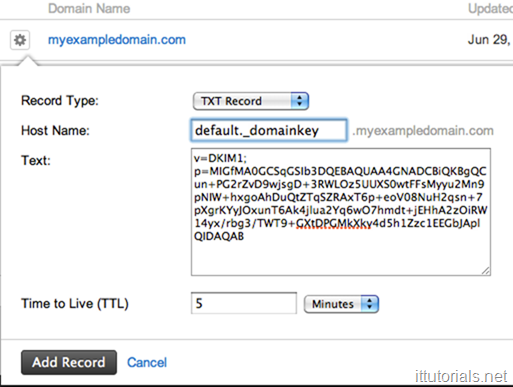
DKIM or DomainKeys Identified Mail is a cryptographic email authentication method designed to detect email spoofing. It allows the receiver to check that an email claimed to have come from a specific domain was indeed authorized by the owner of that domain. It is intended to prevent forged sender addresses in emails, a technique often used in phishing and spoofing emails.
If you are using a cloud-based spam filtering software, most likely you can get the domain keys from them to enter in your domain DNS. Microsoft Exchange 2010 or 2013 doesn’t support DKIM authentication natively, but there are third-party tools you can install to create them. be careful with that though.
A DKIM record looks like this:
And the last thing that almost put the nail in the coffin when it comes to spoofing emails, but it can be the most disruptive on legitimate email flow is DMARC.
DMARC is fairly new in the spam combating arena and is not widely adopted yet that’s why it can be disrupting. DMARC builds upon SPF and DKIM so you need to have those two records implemented first before you get to DMARC your mail server.
DMARC closes the security vulnerabilities inherent in email protocols so it could be the holy grail we’ve been waiting for to put all our spoofing emails woes to rest, but like I said, I don’t think the industry is ready for it yet, so is not widely adopted.
I tried setting up a DMARC record for the company I work for, and because DNS records sometimes can take awhile to replicate, we didn’t see the impact of it until the next day.
It was a chaos, and I sweat my shirt a couple of times
Maybe I didn’t do it right, there is a lot of legwork you have to do before implementing a DMARC record because nothing that has the characteristics of a spoof email will come through, that includes newsletters, emails from spammy looking domains, etc they will be automatically rejected at the domain level, they won’t even hit your spam filter for you to sort through.
There are policies you can set with a DMARC record to minimize the impact, but even with that, it was a chaos for us.
Check online to learn more or how to set up a DMARC record.
So there you have it, my friends, I hope this overview on how to stop spoofing emails is helpful to you. Please hit the “blue helpful button” below if it was. Thank you!