The National Institute of Standards and Technology (NIST) Framework is a comprehensive cybersecurity guide that helps organizations manage and reduce cybersecurity risks. Comprised of three main components—the Core, the Implementation Tiers, and the Profiles—the framework offers a cohesive and adaptable cybersecurity risk management strategy.
In this article, we will focus on the Implementation Tiers component, which assesses the maturity of an organization’s cybersecurity practices. We will explore its structure, purpose, and benefits for organizations looking to improve their cybersecurity posture.
I recommend reading the NIST Core Component article before reading this article
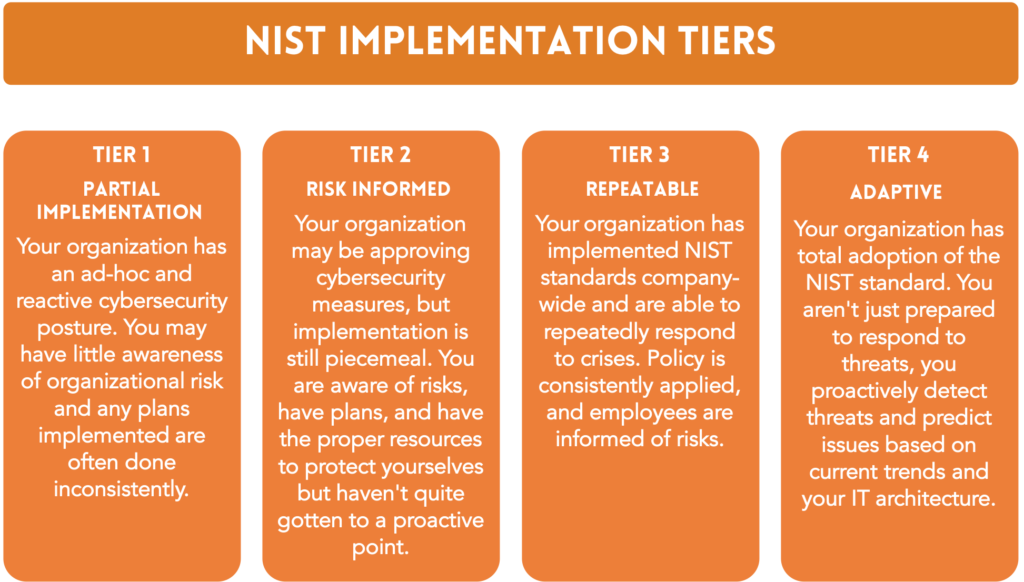
Table of Contents
I. Understanding the NIST Framework Implementation Tiers
The Implementation Tiers are designed to help organizations assess the maturity of their cybersecurity risk management practices. They provide a benchmark for evaluating an organization’s current cybersecurity state and offer a roadmap for improvement. The Tiers range from Tier 1 (Partial) to Tier 4 (Adaptive), reflecting the progression of an organization’s cybersecurity capabilities.
II. The Four Implementation Tiers
Tier 1: Partial
Organizations at Tier 1 have a limited understanding of their cybersecurity risk and have implemented few, if any, formal cybersecurity risk management processes. Cybersecurity activities are typically reactive and performed on an ad hoc basis.
Characteristics:
Lack of a comprehensive risk management program
Inconsistent or nonexistent cybersecurity policies and processes
Limited awareness of cybersecurity threats and vulnerabilities
Reactive response to cybersecurity incidents
Tier 2: Risk-Informed
Organizations at Tier 2 have developed an awareness of cybersecurity risk and have established some formal risk management processes. However, these processes may not be fully integrated across the organization, and coordination between different departments may be lacking.
Characteristics:
Basic risk management program in place
Informal coordination of cybersecurity activities across the organization
Limited use of external threat information and collaboration with industry partners
Some formal policies and processes established, but not consistently applied
Tier 3: Repeatable
Organizations at Tier 3 have a well-defined and consistently implemented cybersecurity risk management program. These organizations proactively manage cybersecurity risks and have integrated risk management processes throughout the organization.
Characteristics:
Comprehensive risk management program with formalized processes
Organization-wide coordination and collaboration on cybersecurity activities
Regular use of external threat information and active engagement with industry partners
Consistent application of cybersecurity policies and processes across the organization
Tier 4: Adaptive
Organizations at Tier 4 have a highly advanced cybersecurity risk management program that continuously evolves to address emerging threats and vulnerabilities. These organizations actively adapt their cybersecurity practices based on lessons learned and predictive indicators, demonstrating a strong culture of continuous improvement.
Characteristics:
Sophisticated and continuously evolving risk management program
Seamless coordination and collaboration across the organization
Advanced use of external threat information and strong partnerships with industry stakeholders
Proactive adaptation of cybersecurity policies and processes based on lessons learned and predictive analysis
III. Benefits of Adopting the NIST Framework Implementation Tiers
The Implementation Tiers offer numerous benefits to organizations looking to improve their cybersecurity posture:
Benchmarking and Self-Assessment: The Tiers provide organizations with a benchmark for assessing their current cybersecurity capabilities and identifying areas for improvement.
Prioritization and Resource Allocation: By understanding their current Tier level, organizations can prioritize their cybersecurity efforts and allocate resources more effectively.
Roadmap for Improvement: The Tiers offer a clear roadmap for organizations to progress from a basic level of cybersecurity maturity to a more advanced, adaptive state.
Consistency and Accountability: By adopting the Implementation Tiers, organizations can establish a consistent approach to cybersecurity risk management and hold themselves accountable for continuous improvement.
IV. Moving Up the Implementation Tiers
To progress from one Tier to the next, organizations should consider the following steps:
- Conduct a thorough self-assessment: Start by evaluating your organization’s current cybersecurity risk management practices, policies, and processes. Identify areas of strength and weakness, and determine which Tier best represents your organization’s current state.
- Develop a plan for improvement: Based on your self-assessment, create a detailed plan outlining the actions required to move your organization up to the next Tier. This plan should include specific goals, timelines, and resource allocations.
- Implement the plan: Execute the improvement plan, taking care to monitor progress and adjust as necessary. Ensure that all stakeholders are aware of the plan and their respective responsibilities.
- Monitor and measure progress: Regularly assess the effectiveness of the implemented changes and measure progress toward achieving the goals outlined in the improvement plan. Adjust the plan as needed to address any gaps or emerging risks.
- Foster a culture of continuous improvement: Encourage a mindset of ongoing learning and adaptation within your organization. Promote the sharing of lessons learned and the use of feedback to improve cybersecurity risk management practices.
V. Balancing Tier Selection with Organizational Needs
It is important to note that not all organizations need to aim for the highest Tier. The appropriate Tier for an organization depends on its specific risk profile, business requirements, and available resources. When selecting an appropriate Tier, organizations should consider factors such as the nature of their business, the sensitivity of the data they handle, and the potential impact of a cybersecurity incident on their operations.
VI. Integration with the NIST Framework Core and Profiles
The Implementation Tiers are designed to complement the other components of the NIST Framework, namely the Core and the Profiles. The Core provides a structured approach to cybersecurity risk management, while the Profiles help organizations customize the framework to their unique needs and priorities. By aligning their cybersecurity practices with the appropriate Implementation Tier, organizations can ensure that their risk management efforts are consistent with the broader NIST Framework.
VII. Conclusion
The Implementation Tiers component of the NIST Framework is a valuable tool for organizations looking to assess and improve their cybersecurity maturity. By understanding the characteristics of each Tier and using them as a benchmark for self-assessment and improvement, organizations can build a more robust and resilient cybersecurity posture. As the digital landscape continues to evolve, adopting the Implementation Tiers in conjunction with the NIST Framework Core and Profiles offers organizations a comprehensive and adaptable approach to addressing emerging threats and vulnerabilities, ensuring the long-term success and security of businesses in the digital age.

